SESSION SIDEJACKING
- What is Sidejacking ?
Sidejacking
is the process of sniffing cookie information, then replaying them
against websites in order to clone a victim’s session. We use the term
sidejacking to distinguish this technique from man-in-the-middle
hijacking. Whereas man-in-the-middle hijacking interferes with the
original session, sidejacking does not. The victim continues to use his
session blissfully unaware that we are also in his account.

SideJacking
works only if the site catches a non-SSL cookie, so any Web site that
uses SSL exclusively would be safe from SideJackers. SideJacking was
first demonstrated by Robert Graham, CEO of Errata Security at Black Hat in 2007.
- Techniques :
All
you need to do in order to sidejack is sniff cookies off the wire and
edit cookies. This can be done with a wide variety of tools.
1.
WinPcap is the industry-standard tool for link-layer network access in
Windows environments: it allows applications to capture and transmit
network packets bypassing the protocol stack, and has additional useful
features, including kernel-level packet filtering, a network statistics
engine and support for remote packet capture.
Download and install Winpcap from here.
2. Graham leveraged the tools Ferret, essentially a packet sniffing tool that captures cookies and writes them to a hamster.txt file, and Hamster, basically a local proxy that creates a web front end for exploiting the cookie information captured by Ferret.
Download and install Ferret ----Hamster from here.
3. Unzip the tools into a directory such as C:\sidejacking.
4. Open a command prompt and change to that directory as cd c:\sidejacking.
5. Use ferret –W to figure out which interface you want to sniff.
2. Graham leveraged the tools Ferret, essentially a packet sniffing tool that captures cookies and writes them to a hamster.txt file, and Hamster, basically a local proxy that creates a web front end for exploiting the cookie information captured by Ferret.
Download and install Ferret ----Hamster from here.
3. Unzip the tools into a directory such as C:\sidejacking.
4. Open a command prompt and change to that directory as cd c:\sidejacking.
5. Use ferret –W to figure out which interface you want to sniff.

6. Use ferret –i n to start sniffing cookies. Here n is the interface number.
7. Now use hamster in the same directory as hamster.txt to start the proxy.

8. Set up a browser to use the proxy at 127.0.0.1:3128.
9. In that browser, go to http://hamster to go to the proxy console window.

10. Select a victim, then click on a URL to sidejack it.

- Countermeasures :
1.
Always try to stick to secured WiFi networks that you know and trust
that would not have any strangers on it running packet sniffers.
2.
Never use a Wi-Fi hotspot unless they are using VPN (virtual private
networking) or SSL (secure sockets layer) to access sensitive
information.
3. Graham said that Google Mail users could switch to https://mail.google.com and secure their session from such snooping.
 ------------------------------------------------------------------------------------------------
------------------------------------------------------------------------------------------------SESSION HIJACKING
- What is Session Hijacking ?
 TCP
session hijacking is when a hacker takes over a TCP session between
two machines. Since most authentication only occurs at the start of a
TCP session, this allows the hacker to gain access to a machine.
TCP
session hijacking is when a hacker takes over a TCP session between
two machines. Since most authentication only occurs at the start of a
TCP session, this allows the hacker to gain access to a machine.- Techniques :
1. Session Fixation:
The session fixation attack is a class of Session Hijacking, which steals the established session between the client and the Web Server after the user logs in. Instead, the Session Fixation attack fixes an established session on the victim's browser, so the attack starts before the user logs in.

For detailed info on How Session Fixation works click here.
2. Session Sidejacking:
where the attacker uses packet sniffing to read network traffic between two parties to steal the session cookie. Many web sites use SSL encryption for login pages to prevent attackers from seeing the password, but do not use encryption for the rest of the site once authenticated. This allows attackers that can read the network traffic to intercept all the data that is submitted to the server or web pages viewed by the client.
1. First the attacker uses a network sniffer to capture a valid token session called Session ID.
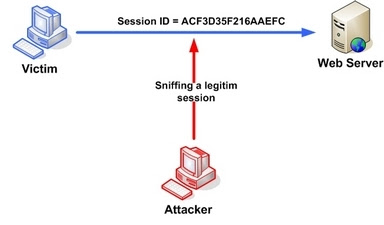 2. Now he manipulates the token session to gain unauthorized access to the Web Server or hijack the victim's web session.
2. Now he manipulates the token session to gain unauthorized access to the Web Server or hijack the victim's web session.
For detailed info on How Session Sidejacking works click here.
3. Cross-Site Scripting:
The attacker can compromise the session token by using malicious code or programs running at the client-side. If an attacker sends a crafted link to the victim with the malicious JavaScript, when the victim clicks on the link, the JavaScript will run and complete the instructions made by the attacker. The example shows how the attacker could use an XSS attack to steal the session token.

For detailed info on How XSS works click here.
- Protection :
2. Some services make secondary checks against the identity of the user. For example it will change the value of the cookie with each and every request.
3. Users may also wish to log out of websites whenever they are finished using them.
4. Encryption of the data passed between the parties; in particular the session key. This technique is widely relied-upon by web-based banks and other e-commerce services.

Happy Hacking...Enjoy...
For educational purpose only...Do not misuse it...






