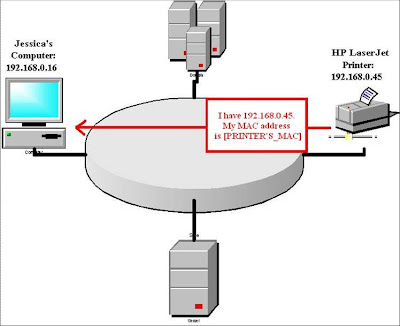
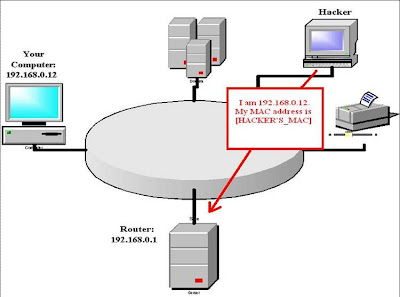
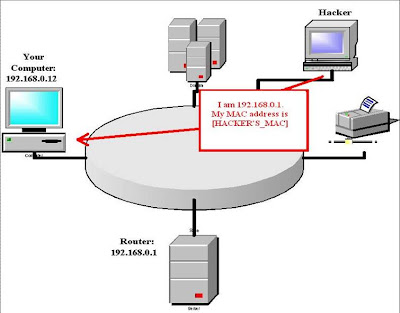
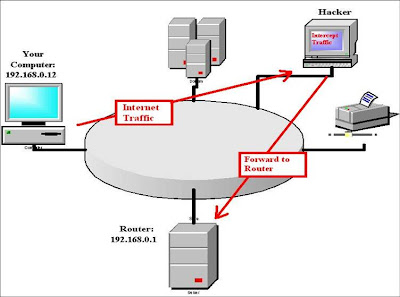
- How does the attack begin ?
Attackers
follow a fixed methodology to penetrate into a system. The steps a
hacker follows can be broadly divided into five phases:
1. Reconnaissance:
Reconnaissance
or Footprinting is consideredthe first pre-attack phase and is a
systematic attempt to locate, gather, identify, and record information
about the target. The hacker seeks to find out as much information as
possible about the victim. Some hackers might dumpster dive to find out
more about the victim. Dumpster diving is the act of going through the victim's trash. Another favorite of the hacker is social engineering.
A social engineer is a person who can smooth talk other individuals
into revealing sensitive information. This might be accomplished by
calling the help desk and asking someone to reset a password or by
sending an email to an insider telling him he needs to reset an
account.
2. Scanning:
Scanning
and enumeration is considered the second pre-attack phase. Scanning is
the active step of attempting to connect to systems to elicit a
response. Enumeration is used to gather more in-depth information about
the target, such as open shares and user account information. At this
step in the methodology, the hacker is moving from passive information
gathering to active information gathering. Hackers begin injecting
packets into the network and might start using scanning tools such as Nmap.
The goal is to map open ports and applications. Unlike the elite
blackhat hacker who attempts to remain stealth, script kiddies might
even use vulnerability scanners such as Nessus to scan a victim's network.
3. Gaining Access:
As
far as potential damage, this could be considered one of the most
important steps of an attack. This phase of the attack occurs when the
hacker moves from simply probing the network to actually attacking it.
After the hacker has gained access, he can begin to move from system to
system, spreading his damage as he progresses. Access can be achieved
in many different ways. A hacker might find a vulnerability in the web
server's software or might perform a denial of service (DOS) on
that server. If the hacker is really bold, he might even walk in and
tell the receptionist that he is late for a meeting and will wait in
the conference room with network access. Pity the poor receptionist who
unknowingly provided network access to a malicious hacker.
4. Maintaining Access:
Hackers
are diligent at working on ways to maintain access to the systems they
have attacked and compromised. They might attempt to pull down the etc/passwd file or steal other passwords so that they can access other user's accounts. Rootkits are one option for hackers. A rootkit is a set of tools used to help the attacker maintain his access to the system and use it for malicious purposes.
5. Clearing Tracks:
Nothing
happens in a void, and that includes computer crime. Hackers are much
like other criminals in that they would like to be sure to remove all
evidence of their activities. Hackers must also be worried about the
files or programs they leave on the compromised system. In order that
the target company’s security engineer or network administrator cannot
detect the evidence of attack, the hacker needs to delete logs files and
replace system binaries with Trojans.
- How do you defend the attack ?
In
order to defend a hacker, you have to think from his/her perspective.
Being an ethical hacker, you will need to be aware of these tools and
techniques to discover their activities and to deploy adequate
countermeasures.

Happy Hacking...Enjoy...






 ------------------------------------------------------------------------------------------------
------------------------------------------------------------------------------------------------ TCP
session hijacking is when a hacker takes over a TCP session between
two machines. Since most authentication only occurs at the start of a
TCP session, this allows the hacker to gain access to a machine.
TCP
session hijacking is when a hacker takes over a TCP session between
two machines. Since most authentication only occurs at the start of a
TCP session, this allows the hacker to gain access to a machine.
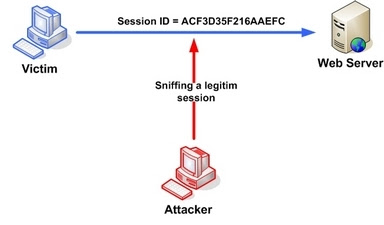 2. Now he manipulates the token session to gain unauthorized access to the Web Server or hijack the victim's web session.
2. Now he manipulates the token session to gain unauthorized access to the Web Server or hijack the victim's web session.




 This
technique can be used to trick a business into disclosing customer
information as well as by private investigators to obtain telephone
records, utility records, banking records and other information
directly from junior company service representatives.
This
technique can be used to trick a business into disclosing customer
information as well as by private investigators to obtain telephone
records, utility records, banking records and other information
directly from junior company service representatives. Vishing or Phone
Phishing is the criminal practice of using social engineering over the
telephone system, most often using features facilitated by Voice over
IP (VoIP), to gain access to private personal and financial information
from the public for the purpose of financial reward.
Vishing or Phone
Phishing is the criminal practice of using social engineering over the
telephone system, most often using features facilitated by Voice over
IP (VoIP), to gain access to private personal and financial information
from the public for the purpose of financial reward.  Baiting is like the real-world Trojan Horse that uses physical media and relies on the curiosity or greed of the victim.
Baiting is like the real-world Trojan Horse that uses physical media and relies on the curiosity or greed of the victim. Kevin David Mitnick
(born August 6, 1963) is a computer security consultant and author. In
the late 20th century, he was convicted of various computer- and
communications-related crimes. At the time of his arrest, he was the
most-wanted computer criminal in the United States.
Kevin David Mitnick
(born August 6, 1963) is a computer security consultant and author. In
the late 20th century, he was convicted of various computer- and
communications-related crimes. At the time of his arrest, he was the
most-wanted computer criminal in the United States. Catch Me If You Can
is a 2002 American biopic-crime film based on the life of Frank
Abagnale Jr., who, before his 19th birthday, successfully conned
millions of dollars by posing as a Pan American World Airways pilot, a
Georgia doctor and Louisiana attorney and parish prosecutor.
Catch Me If You Can
is a 2002 American biopic-crime film based on the life of Frank
Abagnale Jr., who, before his 19th birthday, successfully conned
millions of dollars by posing as a Pan American World Airways pilot, a
Georgia doctor and Louisiana attorney and parish prosecutor.