الحجامة معجزة القرن العشرين أسلوب طبي نبوي لعلاج الأمراض عن طريق تخليص الجسم من شوائب دموية بإزالة الدم المحتبس فيها وزيادة التروية الدموية في المنطقة المرضية .وثبت أنها تؤدي إلى تحريض جهاز المناعة والتخلص من السموم في الجسم وبالتالي سرعة الشفاء.
وردت أحاديث كثيرة في عمل الحجامة وبأنها “خير ما تداوى به الناس” .”في الحجامة شفاء”.
الحِـجامة؟؟يا ترى ماذا تراود إلى فكرك عند قراءة هذه الكلمة؟
قطعة من الفحم الحامي و كأس من الزجاج! بصراحة،هذا ما كان يخطر ببالي كلما سمعت هذه الكلمة! وكنت أنسبها إلى شيوخ كبار السن في الطب الشعبي أيام زمان،و لم يعد لها و جود في العصر الحالي(كما كنت أظن)!!
الحجامه هنا كانت المفاجأة! حين رأيت الصور! بصراحة،،تلك الصور فتحت لي باب جديد للبحث عن كل ما يتعلق بالحجامة! وكنت سعيده و أنا أدخل ذلك الباب،لأني اكتشفت أو بالأحرى اطلعت على أمور جديدة مثيرة في هذا المجال،،فالأمر تجاوز حدود تطبيق علاج نبوي ، إلى براهين لإعجاز السنة النبوية الشريفة !!
لذا أحببت أن أشارككم هذه المعلومات المدعمة بصور حديثة تعرض لأول مرة .و كلي أمل في إضافة معلومة جديدة،أو تصحيح مفاهيم خاطئة حول الحِجامة،و أول هذه المفاهيم هي أن كلمة ‘حجامة’ تـُنطق بكسر الحاء،و ليس بضمها كما هو شائع!!
في البداية: سأطرح نبذة شاملة مختصرة عن الحِجامة ومن ثم: سأعرض الصور مع الشرح أما النهاية: فأتركها لكم ،لتقرؤوها و تتأملوها..و تقولوا سبحان الله!
تاريخ الحِـجامه:
(معلومات أدهشتني و لم أجرؤ على اختصارها)
- وقد عرفها الإغريق القدماءوالصينيون والبابليون ودلت أثارهم وصورهم المنحوتة علي استخدامهمالحجامة في علاج بعض الأمراض،وكانوا في السابق يستخدمون الكؤوس المعدنية وقرون الثيران وأشجار البامبو لهذا الغرض حيث كانوا يفرغونها من الهواء بعد وضعها على الجلد عن طريق مص الهواء .
- وبعد ذلك استخدمت الكاسات الزجاجية والتي كانو يفرغون منها الهواء عن طريق حرق قطعة من القطن أوالصوف أو الورق داخل الكأس .
-كما انتشر استعمالها في عهد ابوقراط وعرفت في فرنسا ، وكان الصينيون يستخدمون تقنية الحجامة فيبعض أنواع العلاجات حيث يتم تقسيم الجسم إلى خطوط ونقاط طاقة ، توضع عليها كؤوس الهواءلشفط الدم الفاسد وبالتالي تنشيط المنطقة المتصلة بالعضو المصاب ،إلا إنها ازدهرت في العصر الإسلامي،و حدد أصولهاحيث وردت في أحاديث الرسول علية الصلاة والسلام حينما قال ( إن كان في شيء مما تداوون به خير فالحجامة)وقال ( ما مررت بملأ من الملائكة ليلة أسرى بي إلا قالوا يا محمد مر أمتك بالحجامة ) وهذا اكبر دليل على أن الحجامة بوركت من قبل الملائكة الكرام .
تعريف الحِـجامة
هي امتصاص الدم بأدة معينة(المِـحجم) بعد تشريط الجلد،و قد تكون جافه بلا دم.الفرق بين الحجامة والتبرع بالدم
الحجامة : هي التخلص من الدم الممتلئ بالأخلاط والغير مفيد للجسم الممتلئ بالشوائب من مواضع مخصصة من الجسم.التبرع بالدم: هو استخراج الدم المفيد من الجسم عن طريق الوريد و إعطائه لشخص محتاج إليه.
أنواع الحِـجامة
1 الرطبة : وهى عمل خدوش بسيطة واستخراج الدم عن طريقها2 الجافة : وهي ما تسمى بكؤوس الهواء وليس فيها إخراج الدم
3المتزحلقة : وهي تدليك باستخدام قارورة الحجامة مع زيت ( الزيتون أو النعناع)
التحليل العلمي لفائدة الحِجامة
(معلومات قيمة جدا و مقنعه أرجو المرور عليها)
2 كل عضو في الجسم له أعصاب تغذية وأعصاب لردود الأفعال ،و المرض يؤثر على الأعصاب الخاصة بردة الفعل التي تسمى (Reflex) ،والحجامة تعمل بشكل فعلي علي مواضع النهايات العصبية لهذه الأعصاب مباشرة.. (الأعصاب الخاصة بردود الأفعال )فمثلا المعدة لها نقطيتن من النهايات العصبية لرد الفعل في الظهر، فعندما تمرض المعدة تجرىالحجامة على هذين المكانين وكذلك البنكرياس له مكانان ، والقولون له ستة أماكن وهكذا ،كل مرض له مكان معين في الجسم هو نقطة النهاية العصبية للعصب الخاص برد الفعل.
3 و الحجامه تعمل على نفس خطوط الطاقة التي تستخدمها الإبر الصينية،لكن عمل الحجامة أقوى..وربما يرجع ذلك إلى أن الإبرة تعمل نقطة صغيرة أما الحجامة فتعمل على دائرة قطرهاخمسة سنتيمترات تقريبا.
فوائـــــــــــــــد الحجامة

بعض فوائد الحجامة :
1- تساعد في تدفق الدم في الأوردة والشرايين بسهولة مما يؤدي إلى تنشيط الدورة الدموية.
2- تنشط الدورة الدموية وإثارة أماكن ردود الفعل في أجهزة الجسم المختلفة مما يساعد على تحسين صحة الإنسان .
3- تقوية المناعة العامة في الجسم وإثارة غدد المناعة ولها مركز في الظهر على الفقرة الرابعة الصدرية .
4- تنشيط أجهزة المخ والحركة والكلام والسمع والإدراك والذاكرة .
5- علاج ظاهر الأثر و مجرب مع الرقية الشرعية لكل من (السحر,الحسد,المس) وننصح به .
بعض الأمراض التي تفيد الحجامة في علاجها بإذن الله :
( أمراض
الدم , ضغط الدم ,الجلطات,أمراض القلب ,الروماتزم ,آلام الركبة ,عرق النسا,انزلاق الغضروف ,آلام الظهر ,آلام الرقبة ,تنميل الأطراف ,آلام الأذن وضعف السمع والطنين ,آلام الجيوب الأنفية ,الصداع النصفي (الشقيقة), الصرع والسحر والحسد, أعراض السكر , النقرس , القولون العصبي , أمراض الكبد , الضعف الجنسي , دوالي الخصيتين و العقم عند الرجال , السكري )
وصدق رسول الله عليه الصلاة والسلام حين قال:( خير ما تداويتم به الحجامة )
مخطط لمواقع الحجامة




مواضع الحِجامة على الجسم

لكن أهم هذه المواضع وهو أيضا المشترك في كل الأمراض وهو الذي يبدؤون به دائماالكاهل :و هو الفقرة السابعة من الفقرات العنقية أي في مستوى الكتف وأسفل الرقبة
فهي تعمل على خطوط الطاقة كالأبر الصينية ولكنها تعطي نتائج أفضل منها بعشرة أضعاف .
تعمل على مواضع الأعصاب الخاصة بردود الأفعال ولكل عضو أعصاب خاصة بتلك العضو ، فالمعده لها مكانان في الظهر وعندما تمرض يتم أجراء الحجامة في هذين الموضعين .
تعمل الحجامة أيضا على الغدد الليمفاوية وتقوم بتنشيطها مما يقةي جهاز المناعه ويزي من قدرتها على مقاومة الأمراض . تعمل الحجامة على الأوعية الدمويه وعلى تنشيط خلايا المخ .
تنشط العمليات الحيوية في طبقات الأنسجة تحت الجلد وبين العضلات .
تقلل حالات الورم الناتج عن ضعف نشاط الدورة الدموية خصوصا أجهاد الساقين والتمزق العضلي والكدمات الشديدة .
جرى الحجامة على كل ذكر بلغ من العمر 22 عاما وكل أنثى تخطت سن اليأس (بأعتبار أن الحيض يغني المرأه عن الحجامة ) وكذلك من لم تبلغ سن اليأس فهذا لا يمنع النساء من الحجامة عند الحاجة اليها .
أفضل وقت للحجامة عندما يميل الجو للدفء فارتفاع الحرارة يجعل الدم أكثر ميوعه وبالتالي سريع الحركة في الأوعية الدموية مما يعرقل تجمع الكريات والشوائب في منطقة الكاهل .
ويراعى عند عمل الحجامة نظافة أدواتها وتعقيمها وتستعمل لمريض واحد فقط ( يفضل وضع شنطه فيها أدوات الحجامة والأحتفاظ بها وأستعمالها للمريض نفسه )
مواضع الحجامة التي ورد أن نبينا محمد صلى الله عليه وسلم احتجمها
احتجم النبي صلى الله عليه وسلم ثلاثا في الأخدعين والكاهل .
احتجم النبي صلى الله عليه وسلم وهو محرم ب(ملل) على ظهر القدم .
احتجم رسول الله صلى الله عليه وسلم وهو محرم في رأسة من داء كان به .
كان النبي صلى الله عليه وسلم اذا اشتكى أحد رأسه قال:اذهب فاحتجم ، وأذا اشتكى رجله قال: اذهب فأخضبها بالحناء .
احتجم رسول الله صلى الله عليه وسلم وهو صائم محرم . ومن أراد الحجامة فليتحر سبعة عشر أو تسعة عشر أو احدى وعشرون ولا يتبيغ بأحدكم الدم فيقتله .
أوقات الحجامة:
حجامة علاجية في حال المرض وتعمل في أي وقت لقول الرسول صلى الله عليه وسلم(إذا هاج بأحدكم الدم فليحتجم , فان الدم إذا تبيغ بصاحبه قتله )الصحيح 3747وكان الإمام احمد – رحمه الله- يحتجم في أي وقت هاج به الدم وفي أي ساعة كانت , ويعني ذلك أنها تعمل في غير ايام السنة المستحبة (17و 19و21) من الشهر الهجري , والمقصود انها تعمل مباشرة عند وجود المرض كما دل الحديث السابق يتبيغ: يثور يتهيج
كيفية عمل الحجامة بالصور

الأمراض التي تعالجها الحِجامة :

تنبيهات هامةقبل الحجامة مراعاة الاتي
يجب لايكون في حالة شبع ولاجوع اي على الاقل ان يكون امتنع عن الاكل لمدة ثلاث ساعات وان لايكون خائفا لا يكون من مرضى الايدزاو الكبد الوبائي أو أية أورام سرطانيةلايكون مريض بالقلب يستعمل جهاز لتنظيم ضربات القلب
لايكون مريضا بالفشل الكلوي يقوم بعملية الغسيل لاتكون حرارته مرتفه أو ان يكون يشعر بالبرودة يدلي بالمعلومات الكاملة عن حالته الصحية بكل دقة فلكل مريض معاملة خاصة تناسب حالته ان تنبيهات وتوصيات هامةيجب مراعاة الاتي قبل الحجامة ب 12 ساعة اخذ فكرة عن الحجامة وعدم القلق بشأنها , والتفكير في فائدتها
النوم والراحة التامة وعدم بذل أي مجهود بدني وعدم الغضب أو التوتر النفسي الامتناع عن الجماع أو التدخين عدم تناول الألبان ومشتقاته وكذلك الدهون والدسم والموالح.
عدم الحضور للحجامة في حالة الشبع او الجوع , ويفضل تناول وجبة خفيفة قبل الحجامة ب 4 ساعات يجب إبلاغ أخصائي الحجامة عن تناول أي علاجات طبية أو الخضوع لجلسات علاجية (طبيعية و نفسية) أو الرقية الشرعية أو عمليات جراحية
القسط البحري – العود الهنديعود القسط Costus
قال صلى الله عليه وسلم : – (( عليكم هذا العود الهندي فإن فيه سبعة أشفية يستعط به من العذرة ويُلد به من ذات الجنب )) متفق عليه .
وقال أيضاً رسول الله صلى الله عليه وسلم ( أن أمثل ما تداويتم به الحجامة و القسط البحري) متفق عليه .
لاشك أن الكلمة الجامعة و الحكمة المختصرة في أحاديث النبي صلى الله عليه و سلم تعني مثالية القسط البحري كدواء لكل داء بدون الأضرار الكيماوية و الآثار الجانبية ( سبعة أشفية لجميع أمراض الإنسان ) .
ويحتوي القسط البحري على مادة الهيلينين و حمض البنزوات وكلاهما من المواد القاتلة للجراثيم ويحتوي أيضاً على الكثير من المواد الفعالة الأخرى . ولذا يفضل عدم تحليته بالسكر لإستخدام الكلور في تبييص السكر .
إستخدامات القسط البحري
1-الشرب : وذلك بطحنه وخلطه مع الماء والشرب منه على قدر المستطاع وهذا لكافة الأمراض كأصل مشترك هو اللدود مع الأصول الأخرى ونذكر هنا ما ذكر من إذابته للجلطة وفائدته للإخصاب ومشاكل الطمث ولإدرار البول و أمراض الكلى و الكبد و سائر أعضاء الجهاز الهضمي و لسرطان الفم و الكوليرا و للرعشة و لاسترخاء الأعصاب و عرق النسا ولتليين الطباع و جيد للدماغ و محرك للشهوة و منشط للجسم وللإستسقاء و قتل ديدان الأمعاء ودفع السم .
و للحمى و تقوية المعدة للأورام و لتقوية جهاز المناعة و لمعالجة نقص المناعة المكتسبة و للنفساء و لمعالجلة الإمساك والإسهال و فاتح للشهية و لإبطال السحر .
2-اللدود : وهو وضع جزء مطحون منه أو شرابه من أحد شقي الفم و هذا لأمراض الجنب كالتهاب الغشاء البلوري و أمراض الرئة عامة3-السعوط : وهو إستنشاق جزء مطحون منه عن طريق الأنف (يستعطى) وهذا لأمراض الجهاز التنفسي عامة كالربو و السل ونزلات البرد و إلتهاب اللوز و التهاب الحلق و البلعوم و للسعال و الحمى
4-التبخير : ذكر الإمامين ومسلم في صحيحهما عن عدم حداد المرأة فوق ثلاث إلا على زوجها . قول رسول الله صلى الله عليه وسلم (( ولا تمس طيباً إلا أدنى طهرها إذا طهرت نبذة من قسط أو أظفار )) فبخور القسط ذو رائحة هادئة طيبة و مطهرة و معطرة للبدن أيضاً . لذا سماه الرسول صلى الله عليه وسلم ( طيباً ) , ولا مانع أن يتبخر به الرجال و الأطفال أيضاً مادام من صنف الطيب وقد وردت أحاديث أخرى تفيد ذلك.
5-التكميد : وهو طحنه وخلط قدر مطحون منه مع قليل من الماء أو العسل ( لبخه) , ثم وضعه على أماكن الحروق و الجروح و البثور و الدمامل و ذلك ككماد ويوضع أيضاً على أماكن الكلف فنزيله بإذن الله
6-التنطيل : و التنطيل جاء من النطل . وهو رش أو غسل الجسم بالماء , و إن كان هذا الماء مشوب بالقسط البحري فإنه سيكون مفيد لقتل الجراثيم و البكتيريا العالقة بجسم الإن
سان و خاصة أماكن الإبطين و بين الفخذين و فروة الرأس و سائر البدن . و كذلك يستخدم كمطهر بصفة عامة .هذا والحمد لله رب العالمينصحيح البخاري و مسلم – الطب النبوي لأبن القيم – فتح الباري تأثير الحجامة على الجن: الجن يتلبس الإنسان لأسباب عدة منها العين والسحر والأذى … الخ ، وذلك في قوله تعالى:”كالذي يتخبطه الشيطان من المس” ويتأثر الجان عندما تستفرغ مادة السحر والعين بالحجامة .
ومن المعلوم أن الجان يجري من ابن آدم مجرى الدم كما ورد في الحديث هذه بعض الأمراض التي تعالج بالحجامة وليست كلها والشافي هو الله عز وجل فهناك حالات شفيت بإذن الله تماما وهناك حالات تحسنت ولله الحمد وهناك حالات لم يكتب لها الله الشفاء فكل شيء بيد الله المرض والشفاء
بقلم: د. منال كمال
 Directed
Harmful High Energy Weapons can be used to destroy electronic devices
and cause severe interference in computers and alarm systems which can
allow forced entry or destruction of vital data. Radar guns are
available from surplus stores most anywhere and can be obtained from
ex-military sources or even police departments. Radar gun power outputs
range from a two or three watts to 3 Megawatts! Portable radar guns
range in size from small hand held devices to vehicle mounted long range
high power models. These devices have very long ranges due to their
greater power, higher frequencies and shorter wavelength. Radar guns
emit long or short pulses of high energy capable of causing instant
damage or death to living creatures. Semiconductor destruction or
malfunction, brain damage & stopping vehicles are other uses for
these devices. Other forms of directed harmful high energy include
devices such as tasers, klystron guns (radar guns), ion beam guns,
plasma pulse guns, soliton bombs, and many more devices.
Directed
Harmful High Energy Weapons can be used to destroy electronic devices
and cause severe interference in computers and alarm systems which can
allow forced entry or destruction of vital data. Radar guns are
available from surplus stores most anywhere and can be obtained from
ex-military sources or even police departments. Radar gun power outputs
range from a two or three watts to 3 Megawatts! Portable radar guns
range in size from small hand held devices to vehicle mounted long range
high power models. These devices have very long ranges due to their
greater power, higher frequencies and shorter wavelength. Radar guns
emit long or short pulses of high energy capable of causing instant
damage or death to living creatures. Semiconductor destruction or
malfunction, brain damage & stopping vehicles are other uses for
these devices. Other forms of directed harmful high energy include
devices such as tasers, klystron guns (radar guns), ion beam guns,
plasma pulse guns, soliton bombs, and many more devices. 


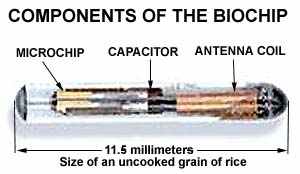
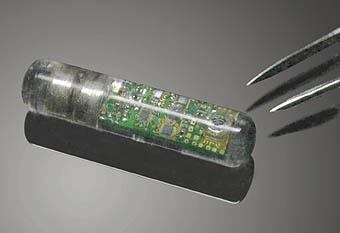
 Implants are without a doubt the most invasive form of harassment.
Electronic implants consist of transmitters, ESF generators,
micro-neurophonic transceivers, tracking devices and other micro sized
devices designed to cause harassment by tracking or controlling movement
and thought. The most common implant was designed many years ago and is
still used to this day. It consists of a unit that is powered by bodily
fluids and is capable of transmitting voice signals, high voltage
pulses, emitting a small tracking beacon signal, or other unspecified
uses (mind control).
Implants are without a doubt the most invasive form of harassment.
Electronic implants consist of transmitters, ESF generators,
micro-neurophonic transceivers, tracking devices and other micro sized
devices designed to cause harassment by tracking or controlling movement
and thought. The most common implant was designed many years ago and is
still used to this day. It consists of a unit that is powered by bodily
fluids and is capable of transmitting voice signals, high voltage
pulses, emitting a small tracking beacon signal, or other unspecified
uses (mind control).