Advanced Electronic Security Co. performs Electronic Sweeping and
Surveys, using the best possible Technical Surveillance Counter Measures
(TSCM), to determine if you're being electronically harassed. We then
proscribe the proper course of action to eliminate the electronic
harassment threat.
What is Electronic Harassment?
If someone uses any electronic device to aid them in invading your person or property for the purpose of gathering information illegally, or for the purpose of causing harm, this is Electronic Harassment.
Electronic Harassment comes in many forms and types. We'll try to explain what they are and what to do about them below.
- Electronic Surveillance
Electronic Surveillance is the imposed observation of a person's belongings, person or surroundings through the use of electronic listening devices, video recording or transmitting devices, spectral imaging through heat or infrared, sound or other radiation sources, and any other means of observing a person's actions, possessions or routines. Not all forms of surveillance use electronic devices and not all forms of surveillance are illegal or considered harassment. Simply observing someone using ones eyes is certainly also considered surveillance and is not illegal in and of itself. Surveillance has become quite advanced and will become more pervasive as our society progresses in technology. Micro recorders, covert hidden video cameras (such as pinhole cameras), ultra tiny microphones, micro transmitters, and other bugging devices are easy to get by anyone at spy novelty shops and online stores. For more on this subject, see Eavesdropping Threats for covert hidden camera pictures with additional information, and Electronic Surveillance page. - Electronic Sabotage/Interference (Jamming)
Electronic sabotage or interference is any sabotage that is intentionally configuring personal property to either be destroyed or malfunction. Any intentional interference such as electronic noise generators, sound generators, light generators, spark gap disrupters, or any other form of EMI (electromagnetic interference) which either destroys, disrupts, causes malfunction or loss of resources is deemed to be electronic harassment. -
Directed Harmful High Energy Devices
This is the most dangerous form of electronic harassment and is quite easy to implement against a person. Directed harmful high energy microwave devices and weapons can include such devices and equipment that are easily available almost anywhere in the World where there are people. Microwave ovens can be modified to focus and direct up to 1200 watts or more, depending on the model, of microwave energy at a person or property and are easy to produce. The results of an attack by a high energy device can be lethal, they can kill or at the least disable a human being or other animals. Attacks from high energy microwave weapons leave blisters, cause internal bruising and/or bleeding, stimulate cancer, cause cataracts, encourage tumors to grow, generate boils, or leave red patches on the skin. Directed Harmful High Energy Weapons will have effective ranges from the point of contact to several hundred yards. Directed
Harmful High Energy Weapons can be used to destroy electronic devices
and cause severe interference in computers and alarm systems which can
allow forced entry or destruction of vital data. Radar guns are
available from surplus stores most anywhere and can be obtained from
ex-military sources or even police departments. Radar gun power outputs
range from a two or three watts to 3 Megawatts! Portable radar guns
range in size from small hand held devices to vehicle mounted long range
high power models. These devices have very long ranges due to their
greater power, higher frequencies and shorter wavelength. Radar guns
emit long or short pulses of high energy capable of causing instant
damage or death to living creatures. Semiconductor destruction or
malfunction, brain damage & stopping vehicles are other uses for
these devices. Other forms of directed harmful high energy include
devices such as tasers, klystron guns (radar guns), ion beam guns,
plasma pulse guns, soliton bombs, and many more devices.
Directed
Harmful High Energy Weapons can be used to destroy electronic devices
and cause severe interference in computers and alarm systems which can
allow forced entry or destruction of vital data. Radar guns are
available from surplus stores most anywhere and can be obtained from
ex-military sources or even police departments. Radar gun power outputs
range from a two or three watts to 3 Megawatts! Portable radar guns
range in size from small hand held devices to vehicle mounted long range
high power models. These devices have very long ranges due to their
greater power, higher frequencies and shorter wavelength. Radar guns
emit long or short pulses of high energy capable of causing instant
damage or death to living creatures. Semiconductor destruction or
malfunction, brain damage & stopping vehicles are other uses for
these devices. Other forms of directed harmful high energy include
devices such as tasers, klystron guns (radar guns), ion beam guns,
plasma pulse guns, soliton bombs, and many more devices.

Directional Microwave EMP Rifle (PARTIAL KIT) Partial kit (shown above). This partial kit will include a 50,000W (yes it says 50KW) Watt X-band military microwave magnetron with complete spec sheets from two manufacturers and operational information to make it work (about 30 pages), EMP rifle plans (over 49 pages), and qty:3 (12KV @ 1A) rectifiers. A device such as this can be made the size of a super soaker water gun, it operates at 9.2GHz and with a properly tuned horn antenna will have an effective range of over 300 yards (possibly more with larger antenna). Such a device could possibly cause semiconductors to burn out, microprocessors to malfunction, inductors to counter induce and create CEMF, induce RF noise, cause ionization of air or gases, cause junction rectification and erase computer data on hard drives, disk and solid state device. Operating such a device may be in violation of State or Federal Laws, consult your Local authority before operating such a device. UPS GROUND SHIPPING ONLY DUE TO INTENSE MAGNETIC FIELD FROM MAGNETRON. Do not purchase this kit if it is illegal to own or operate in your area. (This kit is real and available on the internet. The above photo and description was taken directly from an internet website, but we will not tell you where to find it!)

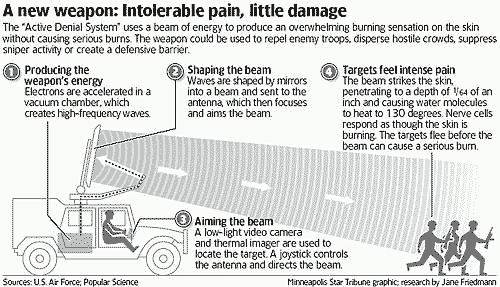
Directed energy weapon for "Active Denial" is now being deployed by the military. - Voice/Data/Image induction
This form of electronic harassment causes an individual to think they are loosing their mind or that they have a mental illness. There are 3 known methods of imposing VDI induction.  Microwave Carrier ULF-UHF Induction Method.
This method utilizes a modulated microwave signal with either an audio,
video, or other form of signal or even data may be used. The microwave
energy with the VDI (Voice/Data/Image) carrier signal is then directed
to the target area or individual. The reaction to this modulated
microwave energy from one individual to another will usually be slightly
different making it very difficult to diagnose as electronic
harassment. The Voice/Data/Image induction form of harassment causes
victims to hear voices in their heads or see random images or lights.
Similar technology was developed to enable communication between humans
and dolphins or even was purported to be used by secret agencies for the
purposes of mind reading and control. A device known as the wireless
neurophone has been patented along with other such devices that perform
similar functions. A microwave carrier ULF-UHF induction device can be
placed at a targets location and operated and monitored remotely.
Transmission locations can be concealed in the same ways that cell
telephone transmission sites so that they cannot be identified easily.
See Stealth for some examples of the way cell antennas can be hidden in plain sight.
Microwave Carrier ULF-UHF Induction Method.
This method utilizes a modulated microwave signal with either an audio,
video, or other form of signal or even data may be used. The microwave
energy with the VDI (Voice/Data/Image) carrier signal is then directed
to the target area or individual. The reaction to this modulated
microwave energy from one individual to another will usually be slightly
different making it very difficult to diagnose as electronic
harassment. The Voice/Data/Image induction form of harassment causes
victims to hear voices in their heads or see random images or lights.
Similar technology was developed to enable communication between humans
and dolphins or even was purported to be used by secret agencies for the
purposes of mind reading and control. A device known as the wireless
neurophone has been patented along with other such devices that perform
similar functions. A microwave carrier ULF-UHF induction device can be
placed at a targets location and operated and monitored remotely.
Transmission locations can be concealed in the same ways that cell
telephone transmission sites so that they cannot be identified easily.
See Stealth for some examples of the way cell antennas can be hidden in plain sight.
- Direct Contact Induction Method. This method requires direct skin contact of the subject. Voice/Data/Image induction (VDI) is induced through the skin, using the natural ability of the skin to conduct energy. The DCI method uses a simple high voltage D.C. carrier, which is modulated with the VDI signal and is coupled to the subject body using capacitive skin pads. The contacts need to contact any part of the skin anywhere on the body. The signal is received and interpreted by the nerves below the skin surface and sent to the brain which processes the information signals, causing the images or sounds or data to appear to the target without the actual use of their eyes or ears. A similar device is also known as the neurophone. There are many patents for similar devices. Evidence of unauthorized use on someone is two or more circular red marks on the skin or two or more blisters.
- Magnetic Pulse Induction Method. The neurons within the
nerves and human brain are very sensitive to magnetic fields. The MPI
method uses an induction coil to induce a low to medium magnetic field
in and around the brain causing the neurons to misroute, slow down or
revert. This form of electronic VDI harassment is often diagnosed as EMI
(electromagnetic interference) sensitivity, which is similar to someone
getting headaches from prolonged usage of cellular phones or nausea
from being around power lines for extended periods of time. Magnetic
Pulse Induction Method may be employed by using a device implanted
within the targets home or surroundings and can be operated remotely.
- Radiation
Radiation is a very common form of harassment. A potential harasser can easily buy an old x-ray gun from a surplus dealer and with only slight modifications use it to bombard a target with deadly amounts of x-ray radiation. Radiation devices can be battery powered and used for long periods of time. High exposure to x-ray radiation will cause tumors, brain disorders, mental illness, tremors, headaches, cataracts, seizures or even death. Radiation harassment is usually done over long periods of time, ranging from days to years, in order to induce harm. Radiation harassers can also get various radioactive materials such as thorium nitrate, plutonium oxide, uranium nitrate, and uranyl nitrite. Using radioactive materials a harasser can cause a terrible and agonizing death. - Implants
 Implants are without a doubt the most invasive form of harassment.
Electronic implants consist of transmitters, ESF generators,
micro-neurophonic transceivers, tracking devices and other micro sized
devices designed to cause harassment by tracking or controlling movement
and thought. The most common implant was designed many years ago and is
still used to this day. It consists of a unit that is powered by bodily
fluids and is capable of transmitting voice signals, high voltage
pulses, emitting a small tracking beacon signal, or other unspecified
uses (mind control).
Implants are without a doubt the most invasive form of harassment.
Electronic implants consist of transmitters, ESF generators,
micro-neurophonic transceivers, tracking devices and other micro sized
devices designed to cause harassment by tracking or controlling movement
and thought. The most common implant was designed many years ago and is
still used to this day. It consists of a unit that is powered by bodily
fluids and is capable of transmitting voice signals, high voltage
pulses, emitting a small tracking beacon signal, or other unspecified
uses (mind control).



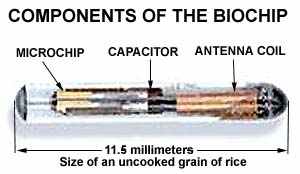
Newest version of a biochip implant. For more information about this chip go to
http://www.nasatech.com/Briefs//May99/ARC14280.html
Millions may be carrying microchips in their bodies worldwide. The Safe Medical Devices Act, which became a law in 1990, requires USA manufacturers of implants and medical devices, to adopt a method for identifying and tracking their products permanently implanted in humans, and to keep track of the recipients, in case malfunctions arise. Breast implants, pacemakers, replacement heart valves and prosthetic devices implanted in millions worldwide are all to be tracked. And one of the methods used to track these devices is implanting microchips which store data about the manufacturer, the surgeon, the date of implant, etc.
- Laser Harassment Devices
The use of simple, easy to procure lasers to harass or "Dazzle" a subject is becoming more prevalent. Subjects of this type of harassment have reported seeing "little red dots" on their curtains, through their windows or on themselves. There have been numerous reports of people being momentarily blinded by red lights (red lasers) while they were driving in their cars. Some of these incidents have resulted in traffic accidents, although no permanent blindness has yet to be reported as a result of being "spotted".

Laser gun sight, zoom rifle scope, 3-axis adjustable tripod head
The parts that make this device can be purchased at any gun store
and the tripod is a standard issue camera tripod.

Hand-held unit with laser gun sight and golf scope
United States Patent 5,629,678
Gargano , et al. May 13, 1997
Personal tracking and recovery system
Abstract
Apparatus for tracking and recovering humans utilizes an implantable transceiver incorporating a power supply and actuation system allowing the unit to remain implanted and functional for years without maintenance. The implanted transmitter may be remotely actuated, or actuated by the implantee. Power for the remote-activated receiver is generated electromechanically through the movement of body muscle. The device is small enough to be implanted in a child, facilitating use as a safeguard against kidnapping, and has a transmission range which also makes it suitable for wilderness sporting activities. A novel biological monitoring feature allows the device to be used to facilitate prompt medical dispatch in the event of heart attack or similar medical emergency. A novel sensation-feedback feature allows the implantee to control and actuate the device with certainty.
Read The Complete Patent Information
Gargano , et al. May 13, 1997
Personal tracking and recovery system
Abstract
Apparatus for tracking and recovering humans utilizes an implantable transceiver incorporating a power supply and actuation system allowing the unit to remain implanted and functional for years without maintenance. The implanted transmitter may be remotely actuated, or actuated by the implantee. Power for the remote-activated receiver is generated electromechanically through the movement of body muscle. The device is small enough to be implanted in a child, facilitating use as a safeguard against kidnapping, and has a transmission range which also makes it suitable for wilderness sporting activities. A novel biological monitoring feature allows the device to be used to facilitate prompt medical dispatch in the event of heart attack or similar medical emergency. A novel sensation-feedback feature allows the implantee to control and actuate the device with certainty.
Read The Complete Patent Information
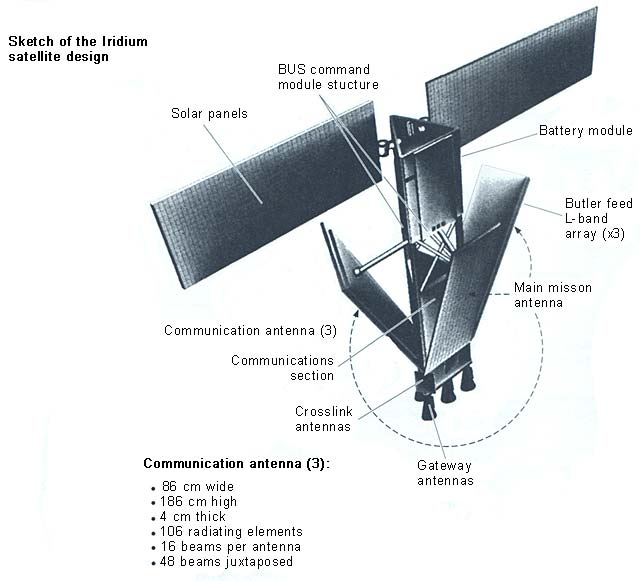
This is one of 66 low-earth orbiting (LEO) satellites comprising the
Iridium satellite system. The original company went bankrupt so the US
Department of Defense assisted in making sure the system stayed in
operation. The system is currently maintained by the Boeing Company.
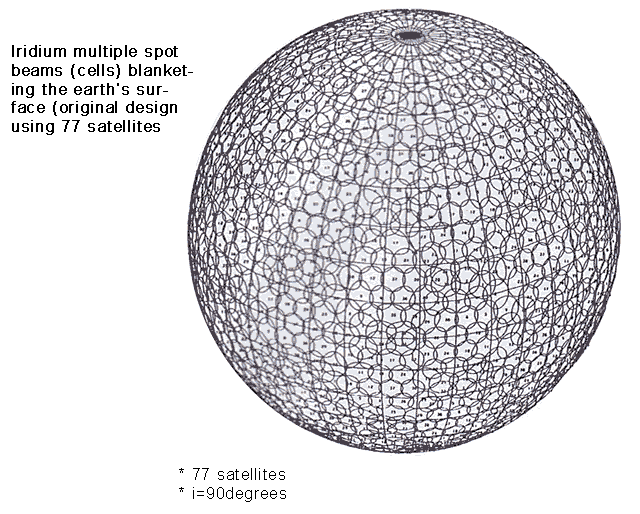
This is a diagram of the planetary coverage of the Iridum system.
This system has transmit and receive coverage of the entire planet. Each
circle is a coverage sector.
Of course there are many other forms of electronic harassment not
mentioned here, but the most common forms of electronic harassment that
you may likely encounter have been covered. Please read Microwave Detection - Remote Mind Control Technology for more on this subject.
Symptoms of Electronic Radiation Exposure
Symptoms may include but are not limited to: Headache,
eye irritation, dizziness, nausea, skin rash, facial swelling, weakness,
fatigue, pain in joints and/or muscles, buzzing/ringing in ears, skin
numbness, abdominal pressure and pain, breathing difficulty, irregular
heartbeat, sexual stimulation and hearing voices (see Patent #4,858,612).
Additional symptoms have been reported in some individuals such as
paralysis, balance problems, body and/or muscle spasms, convulsions,
confusion,depression, difficulty in concentrating, seizure, sleep
disturbances, and memory difficulties.
What Can Be Done To Protect Against Electronic Harassment?
In a legal sense, there isn't too much that can be done.
You could change your venue, relocate or move to avoid the harasser but
this isn't usually a practical method for a variety of reasons.
For starters, the best thing to do is give us a call from a secure phone. We will conduct a sweep of the suspect areas to locate the source of the suspected harassment and then assist in a course of action to stop the harassment.
Natural obstacles are cheap and effective in blocking most X-rays and microwave or RF (could be a radar gun) signals that a harasser might use. Mountains, caves, desert areas, and large lakes or oceans offer excellent protection and can block or distort most forms of electronic harassment.
Shielding signals with Passive or Active shielding can be an effective measure.
If harassment is general to an area and not specifically directed to you, simply moving to another location is the easiest method to stop the harassment. If the harassment is specific to you, then you'll need to employ some sort of shield or cover, such as mountains or a cave. Shielding may be your only alternative to stop the harassment if you cannot employ natural obstacles or shields. Passive shielding is less expensive then Active shielding and consists of special metal materials designed to block high frequency RF energy, X-rays, etc. Active shielding uses sophisticated electronic equipment to jam, capture, redirect, distort or nullify the harmful energy.
For starters, the best thing to do is give us a call from a secure phone. We will conduct a sweep of the suspect areas to locate the source of the suspected harassment and then assist in a course of action to stop the harassment.
Natural obstacles are cheap and effective in blocking most X-rays and microwave or RF (could be a radar gun) signals that a harasser might use. Mountains, caves, desert areas, and large lakes or oceans offer excellent protection and can block or distort most forms of electronic harassment.
Shielding signals with Passive or Active shielding can be an effective measure.
If harassment is general to an area and not specifically directed to you, simply moving to another location is the easiest method to stop the harassment. If the harassment is specific to you, then you'll need to employ some sort of shield or cover, such as mountains or a cave. Shielding may be your only alternative to stop the harassment if you cannot employ natural obstacles or shields. Passive shielding is less expensive then Active shielding and consists of special metal materials designed to block high frequency RF energy, X-rays, etc. Active shielding uses sophisticated electronic equipment to jam, capture, redirect, distort or nullify the harmful energy.
It isn't legal for a private individual, a company or a
corporation to use electronic harassment on you. The military and law
enforcement, however, can use non-lethal weapons (see USC Title 50 Chapter 32 Section 1520a).
Further, testing of electronic equipment; discovering unauthorized electronic surveillance; training of intelligence personnel by officers the United States is allowed.
http://www4.law.cornell.edu/uscode/50/1805.html
Notwithstanding any other provision of this subchapter, officers, employees, or agents of the United States are authorized in the normal course of their official duties to conduct electronic surveillance not targeted against the communications of any particular person or persons, under procedures approved by the Attorney General.
Further, testing of electronic equipment; discovering unauthorized electronic surveillance; training of intelligence personnel by officers the United States is allowed.
http://www4.law.cornell.edu/uscode/50/1805.html
Notwithstanding any other provision of this subchapter, officers, employees, or agents of the United States are authorized in the normal course of their official duties to conduct electronic surveillance not targeted against the communications of any particular person or persons, under procedures approved by the Attorney General.




















